2014 was the year of the data breach. One after another, big brands were subjected to malicious attacks by hackers that not only compromised countless pieces of customer data, but almost-irreparably damaged these brands.
Here are some of the more notable businesses affected by cyber criminal attacks during 2014:
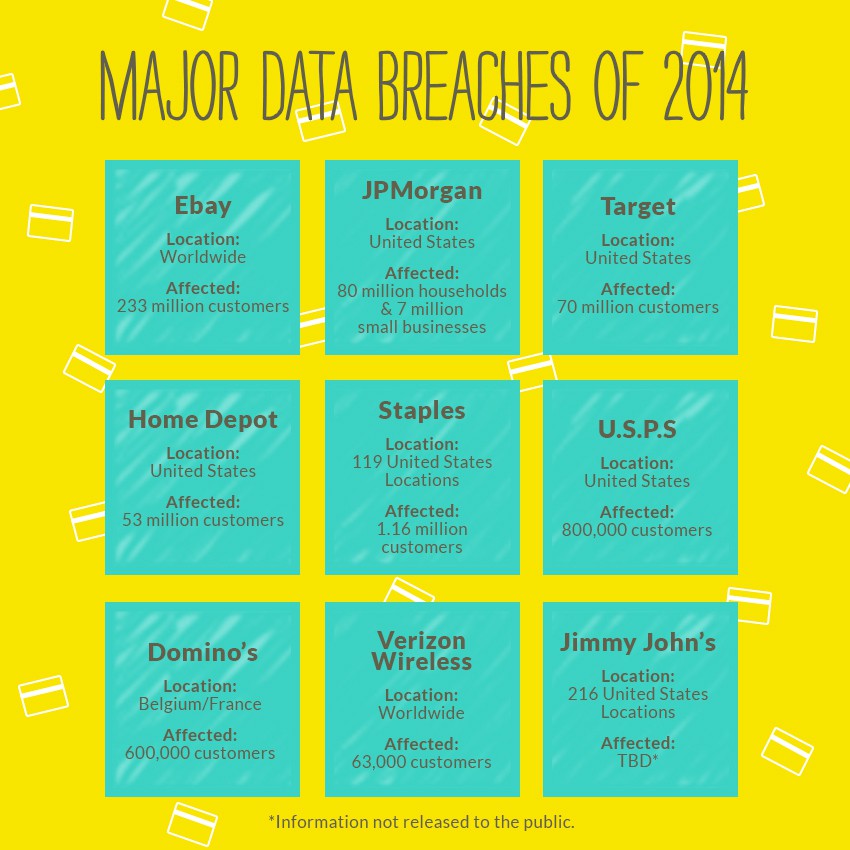
1. Ebay
In May, eBay revealed that hackers had managed to steal the personal records of 233 million users. Usernames, passwords, phone numbers and physical addresses were all compromised. But the biggest victim: Ebay’s ego.
2. JPMorgan
Tens of millions of Chase customers were affected when accounts were infiltrated—even if their bank accounts weren’t. The attack touched 80 millions households and 7 million businesses, making it one of the largest in history.
3. Target
Last spring, Target confirmed that a large data breach from late 2013 affected 40 million customers. The company later announced that more data was compromised, reaching 70 million people. Proving that the shame is 100% on them for exposing customers twice.
4. Home Depot
Home Depot announced last September that their massive data breach allowed cyber criminals to harvest information from 56 million customers in the United States and Canada. Vendor credentials were used to steal customer data.
5. Staples
Staples confirmed its payment system’s data breach–an incident in which 1.16 million credit and debit cards used were stolen over a period of up to six months. The criminals behind the breach have been accused of already using the card data for fraud.
6. U.S.P.S
Hackers attacked the United States Postal Service’s online network. Blame was quickly placed on hackers based out of China. The damage? 800,000 employees’ data was compromised, including Social Security numbers and addresses.
7. Domino’s Pizza
A “hacking group” held Domino’s Pizza hostage, demanding ransom for over 600,000 customer records obtained through a data breach. In exchange for the personal data (names, addresses, emails, phone numbers and even favorite toppings), the hackers demanded $40,000 from the pizza chain.
8. Verizon Wireless
Verizon Wireless experienced 1,367 data breaches and more than 63,000 security incidents in 95 countries during 2014. The company released their annual security report that painted a picture of the reality of data security (or lack there of) and the state of cyber crime.
9. Jimmy John’s
Customers who swiped their cards inside one of 216 Jimmy John’s stores were affected by last year’s data breach. Cards entered manually or online were not included in the attack. The information exposed may include the card number and in some cases the cardholder’s name, verification code and/or the card’s expiration date.
***
Data breaches are the new normal.
So what can you learn from these big brands’ data breach incidents? That no business is truly immune from being the victim of a data breach–but you can practice best standards and practices by having a response plan in place.
Stay updated on payment processing trends by following Abtek on Twitter and Facebook. Sign up to receive our newsletter, too.



 You may have to publicly announce the breach before you have all the facts. Although some people understand that there’s a period of discovery before an announcement can be made, they’re still anxious to learn the facts.
You may have to publicly announce the breach before you have all the facts. Although some people understand that there’s a period of discovery before an announcement can be made, they’re still anxious to learn the facts.