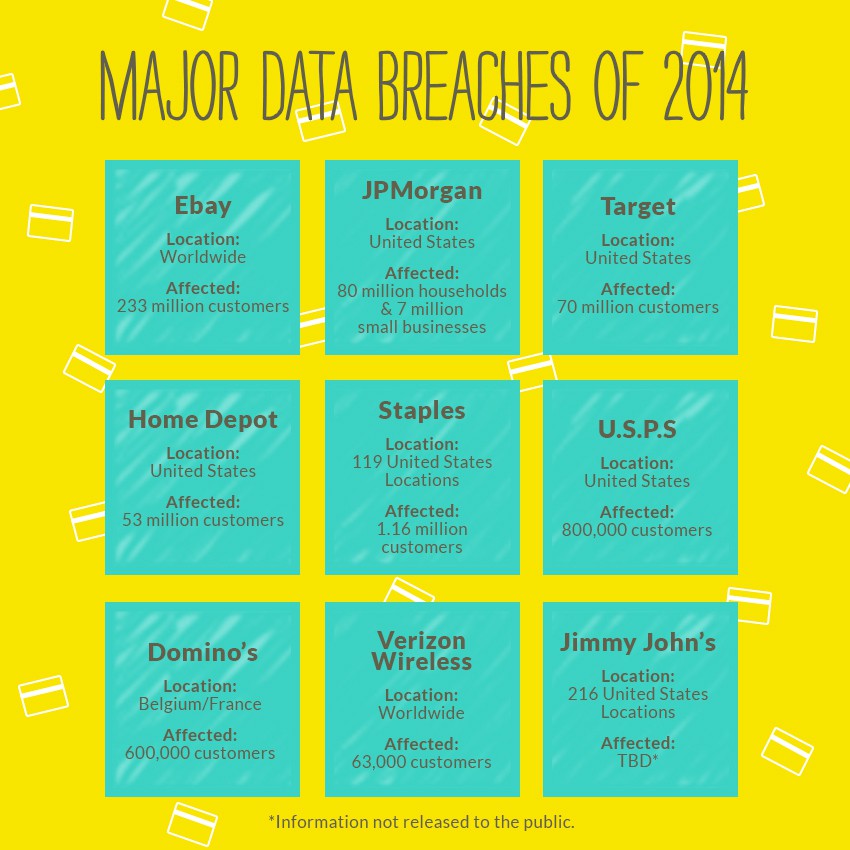
We always stress the importance of having secure payment processing solutions so that you can ensure a positive shopping experience for your customers. But don’t forget: You and your business are consumers, too! It’s important for you to be aware that other businesses’ online platforms might not be as secure as yours. When your data is put into the wrong hands, you could be in for a lot of trouble (i.e. identity theft, stolen credit card information, computer hacks, etc.)
The solution? Good habits help merchants safeguard their sensitive business data online. Below, we’ve put together some of the most effective ways to ensure your online data is safe:
1. Choose a Secure Password
Once upon a time it was acceptable to create a singular password for all online accounts. Your password could even be as simple as your business name! But those days are now far behind us. Today’s hackers are smart and the less secure (complex) your password, the easier it is for them to access your data. The best way to keep your data safe is to choose a unique password for each online account. Your passwords should include a mix of upper and lower case letters, numbers and special characters, if allowed. To make it easy, you can use a password generator, like this one by Norton. Keep in mind: High profile businesses should change their passwords several times a year, according to Credit.com.
 2. Keep Your Email from Getting Hacked
2. Keep Your Email from Getting Hacked
When your business email gets hacked, you can do some serious damage. You might not even know it was hacked until a client asks you why you sent that “super weird video.” Awkward! An email hack can happen to the best of us, but there are steps you can take to prevent it. First, take our advice and change that password! The more secure the better. While you’re on the settings page in your email, see if there’s an option to implement two-step authentication. This links your email account with your phone number, so anytime you (or a hacker!) logs into an “unrecognized” device, you’ll receive a code on your phone to enter on the device in question. Also remember to be smart when opening email, if a message looks iffy, just don’t click on it!
 3. Shop Safely Online
3. Shop Safely Online
First things first when shopping online: Do not ever enter your credit card information on a website if it doesn’t have SSL encryption installed. How can you know if it’s secure? Take a look at the URL—instead of starting with “http://”, it should start with “https://”. Also look for a little lock icon in the URL box. A website with SSL encrypts sensitive information so that only the intended recipient can understand it. In general, go with your gut feeling when shopping online. If a website just doesn’t feel right, find another one that you trust!
 4. Use the Internet for Banking
4. Use the Internet for Banking
Online banking is just so convenient, it’s no surprise that more than 51% of U.S. adults use it. To ensure that your online accounts are as secure as a bank vault, you’ll want to follow some of the tips above, like creating a strong password and enabling two-step verification. On top of that, you’ll want to be sure to always keep your computer software up-to-date and always log out when you’re done.
Today, using the internet to do business is simply part of doing business! Just be sure to use it smartly and you’ll be good to go!
Stay updated on payment processing trends by following Abtek on Twitter and Facebook. Sign up to receive our newsletter, too.